Predictive Analysis to Identifies App Vulnerabilities – DS
When developing an app, numerous errors can affect its performance, ratings, and more. Here, our expert offers insightful points to effectively analyze and identify vulnerabilities in the application.
1) Data Collection
The first step in predictive analysis is collecting the relevant data. It includes information about past incidents, application logs, and user interactions. The quality and quantity of data collected significantly regarding the accuracy of predictive analysis.

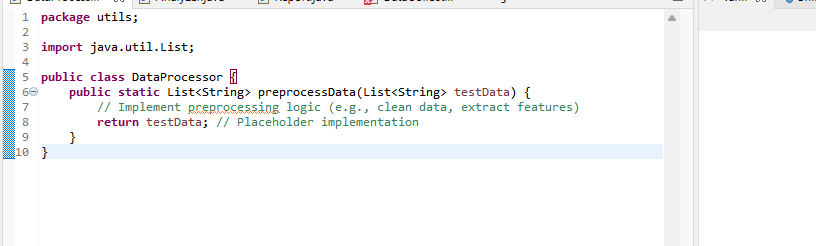
2) Data Preprocessing
Once the data is collected, it goes for preprocessing to clean, transform, and prepare it for analysis. This step involves handling missing values, and normalizing data to ensure consistency and reliability in the analysis process.
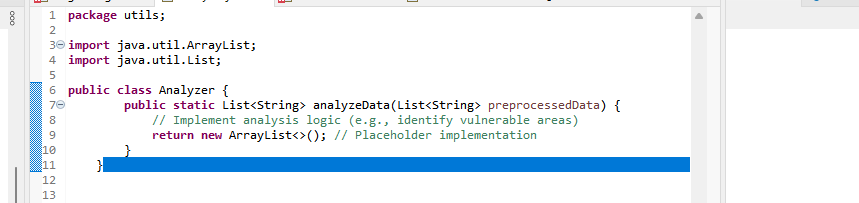
3) Analysis Techniques
Various analysis techniques can be applied to the preprocessed data to identify potential vulnerabilities. These techniques help in uncovering hidden patterns, and trends that may indicate security risks.
4) Vulnerability Identification
Based on the analysis results, vulnerabilities and security weaknesses are identified. These vulnerabilities may include common threats such as cross-site scripting (XSS), authentication flaws, and insecure data storage practices. By pinpointing these vulnerabilities, developers and testers can take proactive measures to address them before they are exploited by malicious actors.
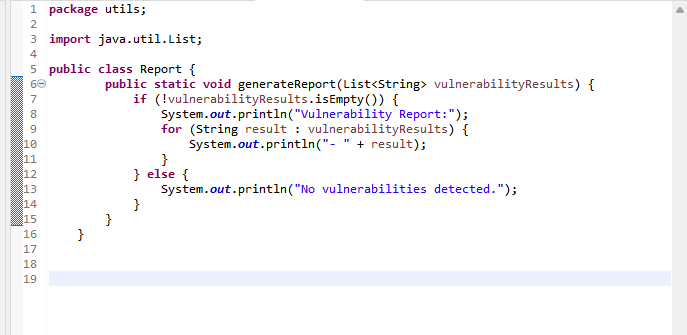
5) Report Generation
The final step in the predictive analysis process is generating a comprehensive report that highlights the identified vulnerabilities and their associated risks. The report provides actionable insights for developers, testers, and security professionals, to prioritize and address security issues effectively.