Security Testing Terminologies and Concepts – DS
Security testing is used to check the vulnerability and loopholes present in the application.
Basic Terminologies of Security Testing
Points that we will be learning about the security testing.
- What are Http and Https?
- How can we avoid man-in-middle attacks?
- Fiddler Demo- Monitoring Network traffic
- Session hijacking and cross-site forgery
- About cookie
- XSS vulnerability
- Parameter tempering
Hypertext Transfer Protocol (HTTP)
When a user sends a request to the server, it uses the HTTP protocol to do so. The server responds back to the client. The response comes in the form of a web page which you see just after typing the web address and pressing “Enter”.
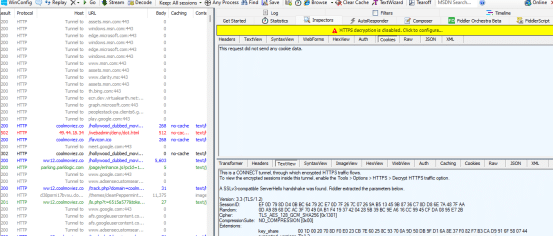
Cons: when we send a request before it goes to the server external people can know the request. They can be your network provider who gives you the wifi connection or with the help of any proxy tool like Fiddler.
Hypertext Transfer Protocol Secure (HTTPS)
HTTPS is a combination of two different protocols. It is a combination of Hypertext Transfer Protocol (HTTPS) and SSL/TLS protocol (Secure Sockets Layer). It is a more secure way to send requests to a server from a client, also the communication is totally encrypted which means no one can know what the user is looking for. Here only HTTPS Protocol is used in Banking websites, payment gateway, emails
How Can We Avoid Man in a Middle Attack?
When a user sends a request SSL encodes that information into one format that only the server can understand so that’s how they will encrypt the information man middle attacks cannot understand the particular code that only the server can understand, so this way
Fiddler Working
People from other machines can capture the traffic from your IP address with the help of these proxy tools
 Session Hijacking and Cross-Site Request Forgery
Session Hijacking and Cross-Site Request Forgery
A CSRF attack forces an authenticated user to send a forged HTTP request, including the victim’s session cookie to a vulnerable web application which allows the attacker to force the user’s browser to generate a request such that the vulnerable app perceives as legitimate requests from the victim.
Suppose I am the user and the attacker forces me to send a forged request through my system
Authcookie: Uses HTTP cookies to authenticate client requests and maintain session information
Net banking Example: A user opens an application to book a train ticket now on popup appears u can win free tickets to some destination , now when user submit the form by clicking on submit button , in the backend attacker makes a code so that the below request hit on hitting a submit button
Banking.com/destinationaccount=8973287932?currency=Dollar?amount=999100/authcookie=7jhy78rew8o7
because he knows how the website works, he knows the website takes requests in this fashion so that’s how he made the replica of the same request this is how the hacker hacked the website and the amount transferred to his account
This call is a forgery request, this is the request made by the attacker with the help of the user.
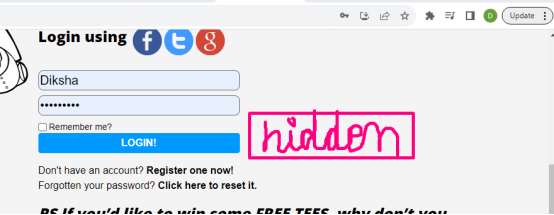
For Developers: how can we avoid cross-site forgeries with Token Mechanism?
There is one hidden field on the login page
What do we need to do as a pen tester to check CSRF
- Check whether the confidential part is going as part of the POST
- Change the token value check and send the request it should not accept
- Open the site in other systems, get the token now hit the use the same token, and use it in the current ID
XSS Vulnerability
Cross-site scripting also known as XSS, is one of the most common web application vulnerabilities that allows a hacker to run his own scripts (especially JavaScript) into web pages viewed by other users. To get detailed information on Cross-Site Scripting (XSS) Attacks & prevention feel free to read our other blog.
Where the Attacker Can Run His Scripts?
- url post string https://www.google.co.in/#q=web+application
- Form submission
- TextAreas
Points to remember
Edit boxes should not allow HTML language to be submitted on their server, if this allows then the hacker will come and write his JavaScript code with HTML to inject into their web application to get the cookies, session ID, user ID, and password, developer should keep tight filter to cut down this HTML and JavaScript code to enter into that server, if they do that in a perfect manner that means we cannot perform XSS Scripting in the application
Note: The information that we are entering is sitting on the server, so we can easily damage it but if there is tight validation in the application then it is not easy to hack it
Detecting XSS Vulnerability for Websites
We will check whether the application fields are accepting HTML code or not
If not then it’s good, but if yes then there is something fishy.
On some other websites what was happening, as they brought the user to 500 and 400 pages, the application should be designed like that
It is correct if it’s not accepting the HTML code but it is not designed well from the user’s perspective
We will check whether the application URLs are accepting HTML code or not. If not then it’s good.
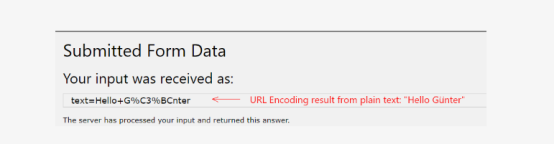
Encoding all the inputs to avoid attack:
It is accepting the <i>hello</i> but not executing it
ACCOUNT SECURITY:
Password Security is driven by two factors:
- Strength of Password
- Uniqueness of password
Check your Password strength from here:
- passwordmeter.com
List of Passwords:
###a class=”external-link” href=”https://dazzlepod.com/site_media/txt/passwords.txt” rel=”nofollow no-referrer” target=”_blank”>https://dazzlepod.com/site_media/txt/passwords.txt
Sources of Attacking Passwords
- Man in the middle attack
- Password retrieved as a cookie with XSS
- Admin facility compromised
Practices to Secure Account Details
- Emailing credentials on account creation
- Forgot password message display methods
- Password reset mail consequences
If the user clicks on the reset password link then the account should not lock immediately, it happened with one of the websites when a user tried to click on the password reset link, their account got logged out then and there and won’t be able to log with the old password
- Password storage Pattern: password should encrypt
- Remember me Password
- Re-authenticate a few important features
Re-authentication is important if the website is related to transactions or has some other confidential detail
For example -when u reset the password it should ask you to enter the old password
or when we do any transaction it should ask for a password or OTP
- Brute force attack handling Mechanism: when the user tries to log in with the different combinations of username and password and suddenly if one password gets clicked it will log in this is called a brute force attack
If the attacker attacks the website with thousands of passwords simultaneously then this is called a brute force attack
So there should be a validation to lock the account after 3, or 4 wrong attempts if there is no feature of locking people will try thousands of password
Parameter Tampering
Parameter tampering is a form of Web attack in which certain parameters in the Uniform Resource Locator or Web page form field data entered by a user are changed without that user’s authorization.
This tampering can often be done with:
- Cookies
- Form Fields
- URL Query Strings
- HTTP Headers
- http://banking.com/id-=12354
Connect with Devstringx Technologies top security testing company & get a free consultation to shield your information and data from cyberattacks.