What is Clickjacking | Clickjacking Attack & Mitigation | Devstringx
What is a Clickjacking Attack?
Clickjacking is a security testing type of attack that finds tricks to trick a user into clicking a webpage element that is not visible or disguised as a different element. This can cause users to unwittingly download any malware, can go to visit malicious web pages, provide sensitive information, transfer money, or purchase products online.
Mostly, clickjacking attacks perform by an attacker on a page that is not a visible page or HTML element, inside the frame, on top of the page the user sees. The user trusts if they are clicking the visible page but in reality, they are clicking an invisible element in the additional page transposed on top of it.
The invisible web page which is in an iframe can be a malicious page or a legitimate page the main user did not intend to visit. For example, a page on the user’s banking web page that authorizes the transfer of money.
Different Variations in the Clickjacking Attack
-
Likejacking
A clickjacking technique in which the Facebook “Like” button or anywhere Like buttons can manipulate by an attacker causing users to “like” a page they actually did not intend to like.
-
Cursorjacking
A UI redressing clickjacking technique that changes the cursor on mouse hover for the position the user perceives as different positions. It relies on security vulnerabilities in Flash and the Firefox browser, which have now been fixed.
Clickjacking Attack Example
- The hacker creates an attractive page that promises to give the user a free trip or other benefits.
- In the background the hacker verifies if the user logged into his banking site and if so, loads the screen that enables the transfer of funds, using query parameters to insert the attacker’s bank details into the form on the user’s banking web page that authorize the transfer of money.
- The bank transfer page is shown as an invisible iframe above the free gift offer page, with the “Confirm Transfer” button aligned over the “Receive Gift” button visible to the user set by the attacker and user unknown about this.
- The user mostly visits the websites and generally clicks on the “Book My Free Trip” button.
- In the real situation, the user is clicking on the invisible iframe and clicks the “Confirmed Transfer” button. Funds transfer to the attacker.
- The user moves forward to a page where information shows about the free gift (not knowing what happened in the background).
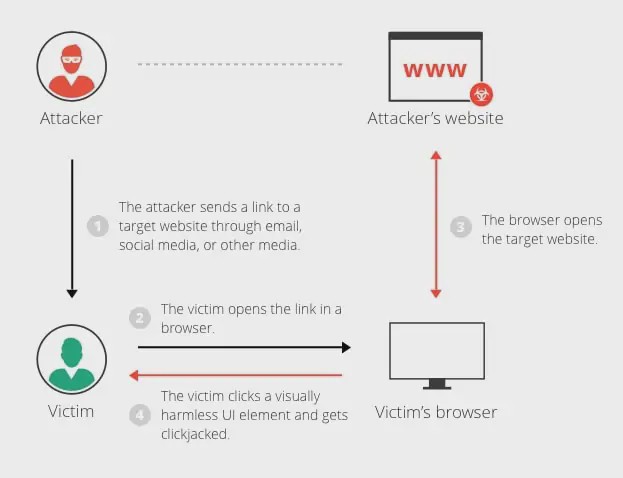
This example explains that, in a clickjacking attack, the malicious action (on the bank website, in this case) can not trace back to the hacker. The reason because the user performed it while being legitimately signed in to their personal account.
Clickjacking Mitigation
There are two common ways to defend against clickjacking:
1) Client-Side Methods
The most common way is called Frame Busting. Client-side methods can be effective in some different ways. Mostly they don’t consider the best practices because they can easily bypass them.
2) Server-Side Methods
The most common way to defend is X-Frame-Options Server-side methods are proposed by software security testing experts as a more effective way to defend against clickjacking attacks.
Read Also:- What Is a CSRF Attack and How to Prevent It
Mitigating Clickjacking with X-Frame-Options Response Header
The X-Frame-Options in the clickjacking response header pass as part of the HTTP response of any website, indicating whether or not a browser should allow rendering a page inside a <FRAME> or <IFRAME> tag.
Below are three values that allow for the X-Frame-Options header in clickjacking:
-
DENY
Does not allow any domain to show this page within a frame
-
SAMEORIGIN
This allows the current web page to be shown in a frame on any other web page but only within the current domain.
-
ALLOW-FROM URI
This allows the current page to be shown in a frame, but only in a specified URI.
Using the SAMEORIGIN Option to Defend Against Clickjacking Attack
X-Frame-Options allows content publishers to prevent their self-content from using in an invisible X frame by hackers for clickjacking.
The DENY option is the most secure and prevents any use of the current page in a frame. More commonly, SAMEORIGIN uses, as it enables the use of X I-frames, but limits them to the current domain.
Limitations of X-Frame-Options
- To enable the SAMEORIGIN option on any web page, the X-Frame-Options header needs to return as part of the HTTP response for each particular page (cannot apply cross-site).
- X-Frame-Options does not support a whitelist of allowed domains. So if it doesn’t work with multi-domain websites that need to display framed content between them.
- There is a limitation and Only one option can use on a single page. For example, it is not possible for the same page to display as a frame both on the latest website and an external website.
- The ALLOW-FROM option does not support by all web browsers.
- X-Frame-Options deprecate option in most browsers.
Clickjacking Testing – Is Your Site Vulnerable?
A very basic and common way to test if your website is vulnerable to clickjacking attacks is to create an HTML page. Then attempt to include a sensitive page from your website in an iframe. It is important to run the test code on any other web server. It’s important because this is the typical behavior in a clickjacking testing attack.
Use the below code the following provided as part of the OWASP Testing Guide:
<html> <head> <title>Clickjack test page</title> </head> <body> <p>Website is vulnerable to clickjacking!</p> <iframe src=”http://www.yoursite.com/sensitive-page" width=”500″ height=”500″></iframe> </body> </html>
Look at the HTML page in a browser and evaluate the page as follows:
- If the text “Website is vulnerable to clickjacking” appears on any web page and below it. You see the content of your sensitive page, the page is vulnerable to clickjacking.
- If only the text “Website is vulnerable to clickjacking” appears on any web page. You do not see the content of your sensitive page. The page is not vulnerable to the simplest form of clickjacking.
However, additional testing requires to see which anti-clickjacking methods use on the web pages whether. They can bypass attackers for clickjacking.
Read Also:- How to Use Brute Force Attack?
How Imperva Helps Mitigate Clickjacking Attacks?
To find the point of clickjacking a site, the site will have to compromise by WAF (Web Application Firewall) prevents. You need to make sure that your website resources are sent to the proper X-Frame-Options HTTP headers. Which would prevent some parts of your site from being framed on other pages or outside your domain.
FAQ’s
- What is the difference between clickjacking and phishing?
Phishing scams are slightly different from clickjacking methods because they interact directly with the victim. In most cases, attackers send fake emails to legitimate companies and trick people into responding with personal information.
- What is the difference between clickjacking and CSRF?
Clickjacking is relevant to CSRF because an attacker attempts to force the web browser to make a request to a web application that the user does not authorize or launch. CSRF places secret requests in iframes, images, or similar tags that browsers load as part of a page.
- Is clickjacking a vulnerability?
As the clickjacking test is a relatively new malicious technique. The damage caused by this clickjacking test code vulnerability is not well known.
- How to perform a clickjacking attack?
Typically, a clickjacking mitigation attack is done by displaying a hidden page or HTML element in an iframe at the top of the page for the user to see. The user thinks he is clicking on the displayed page. But he is clicking on a hidden element on the attached page above.
- How to prevent clickjacking?
There are three main ways to prevent clickjacking. Tells the browser not to accept frames from other domains by sending the correct Content Security Policy (CSP) frame ancestor directive response headers. The old X-Frame-Options HTTP header uses for compatibility between Graceful Degradation and older browsers.