A Detail Tutorial On HTML Injection, Example, Prevention, Mitigation – DS
What is HTML Injection?
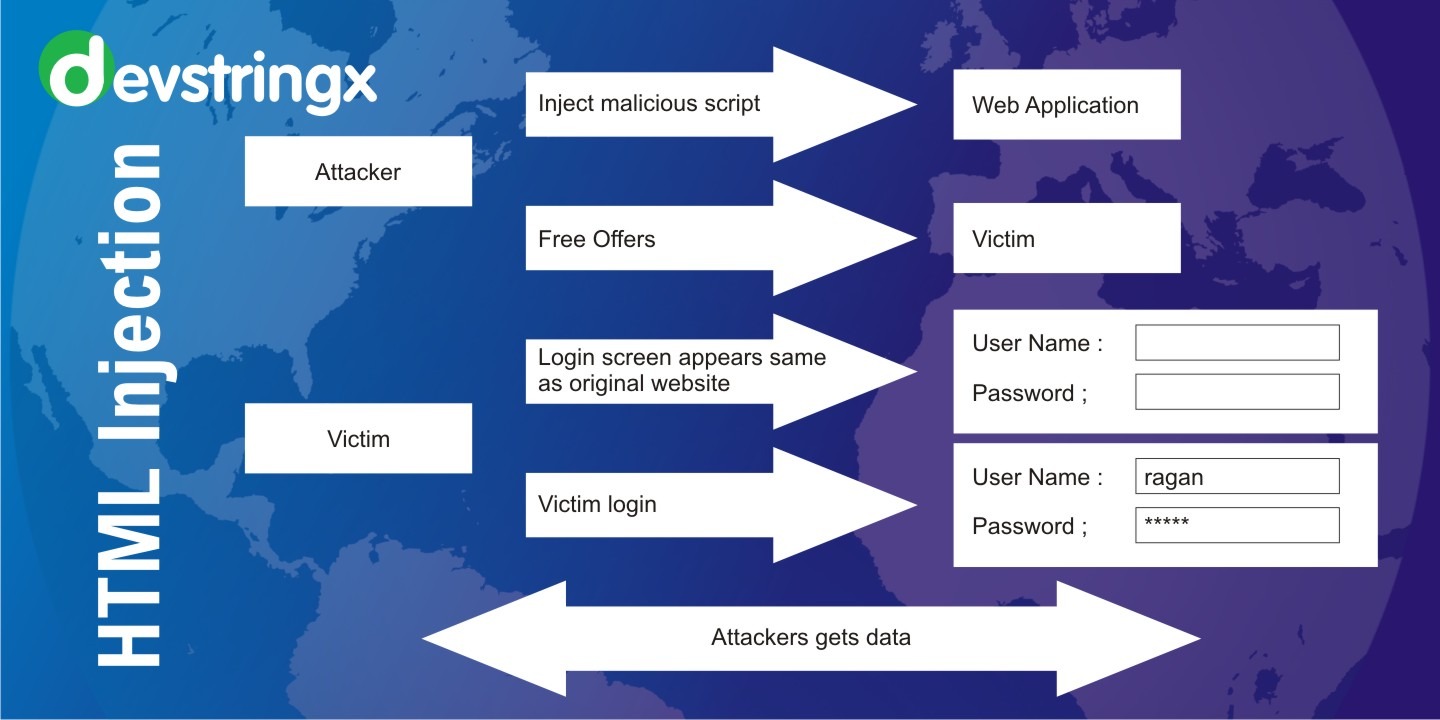
This HTML injection attack is injecting HTML code through the vulnerable parts of the website. The Malicious user sends HTML code through any vulnerable field with the purpose to change the website’s design or any information that is displayed to the user. As a result, the user may see the data that was sent by the malicious user. Therefore, in general, HTML Injection is just the injection of markup language code to the document of the page.
What Is HTML?
To get a better understanding of HTML Injection, firstly we should know about HTML.
HTML is a markup language, where all the website’s elements are written in the tags. Web pages are sent to the browser in the form of HTML documents.
Types of HTML Injection
-
Stored HTML Injection
-
Reflected HTML Injection
#1) Stored HTML Injection: Stored Html injection attack occurs when malicious HTML code is saved in the web server and is executed every time when the user calls an appropriate functionality.
#2) Reflected HTML Injection: In the Reflected Html injection attack case, malicious HTML code is not being permanently stored on the web server. Reflected Injection occurs when the website immediately responds to the malicious input.
This can be again divided into more types:
- Reflected GET
- Reflected POST
- Reflected URL
For Example, I check the source code for the inquiry form on the Devstringx site and find what method is being used for it, then the appropriate HTML Injection method can be selected accordingly.
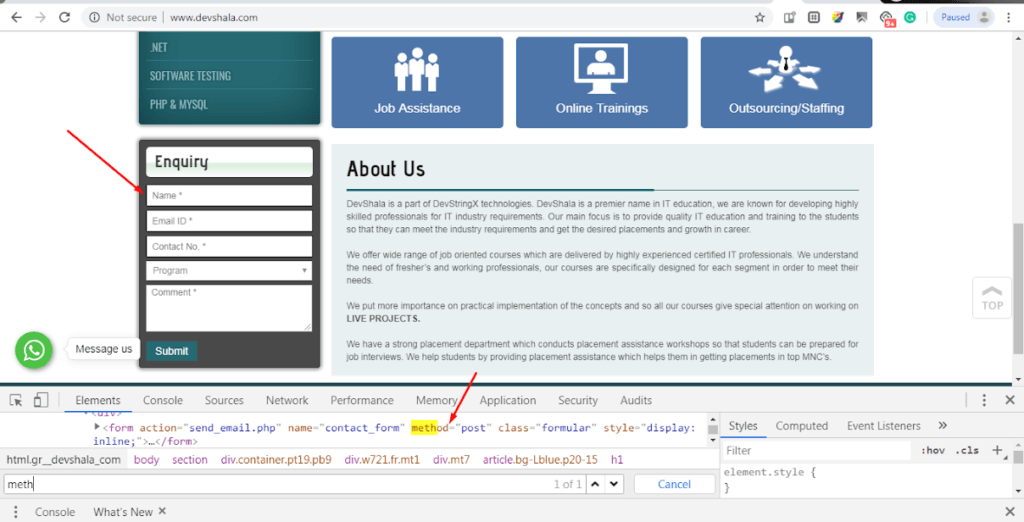
How is HTML Injection Performed?
In this type of attack malicious user targets vulnerable parts of the website. Vulnerable parts of the website may be data input fields and the website’s link. The malicious HTML code can get into the source code by innerHTML. Let’s remember, that inner HTML is the property of DOM documents and with inner HTML, we can write dynamic HTML code. It is used mostly for data input fields like comment fields, questionnaire forms, registration forms, etc. Therefore those elements are most vulnerable to HTML attack.
Suppose, we have a questionnaire form, where we are filling in appropriate answers and our names. And when the questionnaire is completed, an acknowledgment message is displayed. In the acknowledgment message, the indicated user‘s name is also displayed.
The message may look as shown below:
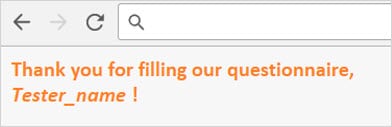
How to Test against HTML Injection?
When testing manually if an HTML Injection is possible, then simple HTML code could be entered – For an HTML injection example, check if the text would be displayed. There is no point to test with a very complicated HTML code, the simple code may be enough to check if it is being displayed.
For Example, it may be simple tags with text: <h1>HTML Injection testing</h1>
If HTML code being saved somewhere is displayed, then the tester can be sure, that this injection attack is possible. We can also find some online scanning tools, where you only have to provide the website’s link, and scanning against HTML attacks will be performed.
Recommended to Read:- What Is Clickjacking Attack and How Do You Prevent It?
How to Prevent HTML Injection?
This type of Html injection attack occurs when the input and output are not properly validated. Therefore the main rule to prevent HTML attacks is appropriate data validation.
Every input should be checked if it contains any script code or any HTML code. Usually, it is checked, if the code contains any special script or HTML brackets – <script></script>, <html></html>
Comparison with other Attacks
In comparison with the other possible Html Injection attacks, this attack definitely will not be considered as risky as SQL Injection or JavaScript Injection attacks, or even XSS may be. It will not destroy the whole database or steal all the data from the database. However, it should not be considered insignificant.
Conclusion
As we have analyzed, with this type of Injection the whole design of your website may be destroyed or even the user’s login data may be stolen. Therefore it is highly recommended to include HTML Injection in security testing.
FAQs
- How to prevent HTML injection in PHP?
Five methods to avoid code injection when developing PHP applications
- exec(), shell exec(), system(), and passthru should not be used ()
- Do not sanitize using strip tags()
- Serialisation of codes
- Implement a PHP security linter
- Make use of a SAST tool to find code injection problems
- How to prevent javascript injection?
- Avoid eval(), setTimeout() and setInterval()
- Eliminate new Function ()
- Avoid JavaScript code serialization.
- Utilize a security linter for Node.js
- To identify and resolve code injection problems, use a static code analysis (SCA) tool.